Maria Holler
Recent Posts
Three Key Steps to Protect Your Members' Passwords from Hackers
August 16, 2017 / by Maria Holler posted in BlindHash Technology
McConnell Golf Selects BlindHash to Make Members’ Online Passwords Virtually Impossible to Steal
August 8, 2017 / by Maria Holler posted in BlindHash Technology
Leading Golf Club Operator Implements New Technology that Prevents Hackers from Compromising Member Accounts.
Data Breaches Happening at Record Pace, Three Key Steps to Protect Your Site
July 25, 2017 / by Maria Holler posted in BlindHash Technology
3 Key Steps to Protecting Your Website From Hackers:
According to a recent NBC news report, data breaches in the U.S. jumped 29% in the first half of 2017. Yet businesses are still opting for convenience over security and thus putting themselves, their future, and their customers in harm's way.
Here are three easy steps to take to protect your website from hackers.
#1: INSTALL AN SSL CERT ON YOUR SITE
When a site begins with https://, it indicates that an SSL cert has been installed on the site. According to hostgator, if you have an online store, or if any part of your website will require visitors to hand over sensitive information like a credit card number, you have to invest in an SSL certificate. The cost to you is minimal, but the extra level of encryption it offers to your customers goes a long way to making your website more secure and trustworthy.
#2: INVEST IN SECURITY PLUGINS
Not all companies have the resources to invest in a full IT team, and thus must rely on security plugins to ensure their website is safe. Depending on your website platform (Wordpress, Magento, shopify, nopCommerce, etc.), there are numerous companies such as BlindHash that offer additonal security layers at reasonable rates to ensure you are protecting yourself against a possible breach.
#3: KEEP YOUR SITE UP TO DATE
It may seem obvious, but ensuring your website is up to date on the latest version of your software platform keeps hackers on their feet. By having the newest version of your platform installed you are minimizing the risk that you’ll be hacked and besides updates usually take very little time to complete.
WHY SECURITY BY OBESITY?
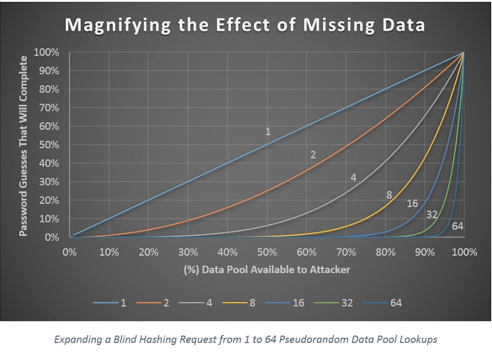
With typical password hashing, each user has his or her own salted hash that can be individually stolen and attacked. The amount of data that must be stolen is miniscule, and high-value users can be targeted by stealing just a few bytes.
Three Reasons Why You Should Use BlindHashing to Protect Your Passwords
July 12, 2017 / by Maria Holler posted in BlindHash Technology
Cybersecurity is constantly changing making it difficult to ensure your data and passwords are secure. As a consumer, it is becoming increasingly onerous to remember your password with the various password combination rules required. As a business with a login page, the PR nightmare that ensues when a breach occurs makes it critical to have the proper cyber security plan in place.
For many years, best practice has been to protect passwords by using computational power to slow down the hashing process. However, with all of the complex hashing techniques available today, one thing is forgotten; where the actual password is stored. This is where BlindHash comes into play. When BlindHash is implemented as an additional tool to your password security defense network, passwords become virtually impossible to be stolen via an offline dictionary attack.
SO WHY SHOULD YOU USE BLINDHASH? THE BETTER QUESTION IS ...
We are very excited to announce that we are a 2016 Platinum MassChallenge award recipient. BlindHash, a Taplink Company, was selected from 1,700 applicants and will receive a $75,000 cash prize. The announcement was made on Nov. 2nd at the annual MassChallenge Awards at the Boston Convention and Exhibition Center. Password database breaches continue to be an achilles heel for many large organizations. In September, Yahoo announced that hackers had stolen information from a minimum of 500 million accounts in late 2014, including passwords. Click here to read the full release.
This year’s Ponemon Institure study found the average consolidated total cost of a data breach grew from $3.8 million to $4 million. The study also reports that the average cost incurred for each lost or stolen record containing sensitive and confidential information increased from $154 to $158. BlindHash can can help reduce your company's risk by eliminating the threat of an offline attack. Click here to read the full Data Breach Report.